Cognitive Data to
Enhance Your Cyber Defense
Use Cyber-psychology to Outsmart Social Engineering.
Trusted Collaborators
























The Reality of Cyber Threats
Technical and behavioural solutions are only 50% of the game. The rest comes down to the human element — where stress, fatigue, and social engineering make organizations most vulnerable.
Social engineering exploits human trust and decision-making under pressure
Burnout and fatigue increase the likelihood of costly mistakes
Lack of visibility into human risk prevents proactive action
Generic, one-size-fits-all training rarely changes real-world behaviour
Successful cyberattacks are caused though social engineering
(Verizon, 2024)
Targeted users fell for phishing in 2022
(Proofpoint, 2022)
Generative AI is hyper-personalizing social engineering and scams
(Koskisali & Carruthers, 2023)
Your Cognitive Risk Reduction Pathway
Transform your organization's security posture through our scientifically-backed three-step approach
ASSESS
Cognitive Vulnerabilities
SCAMBEAT™ Engine
Our proprietary assessment engine analyzes 8 cognitive vulnerability markers to create comprehensive risk profiles. Discover hidden blind spots in your organization's human firewall.
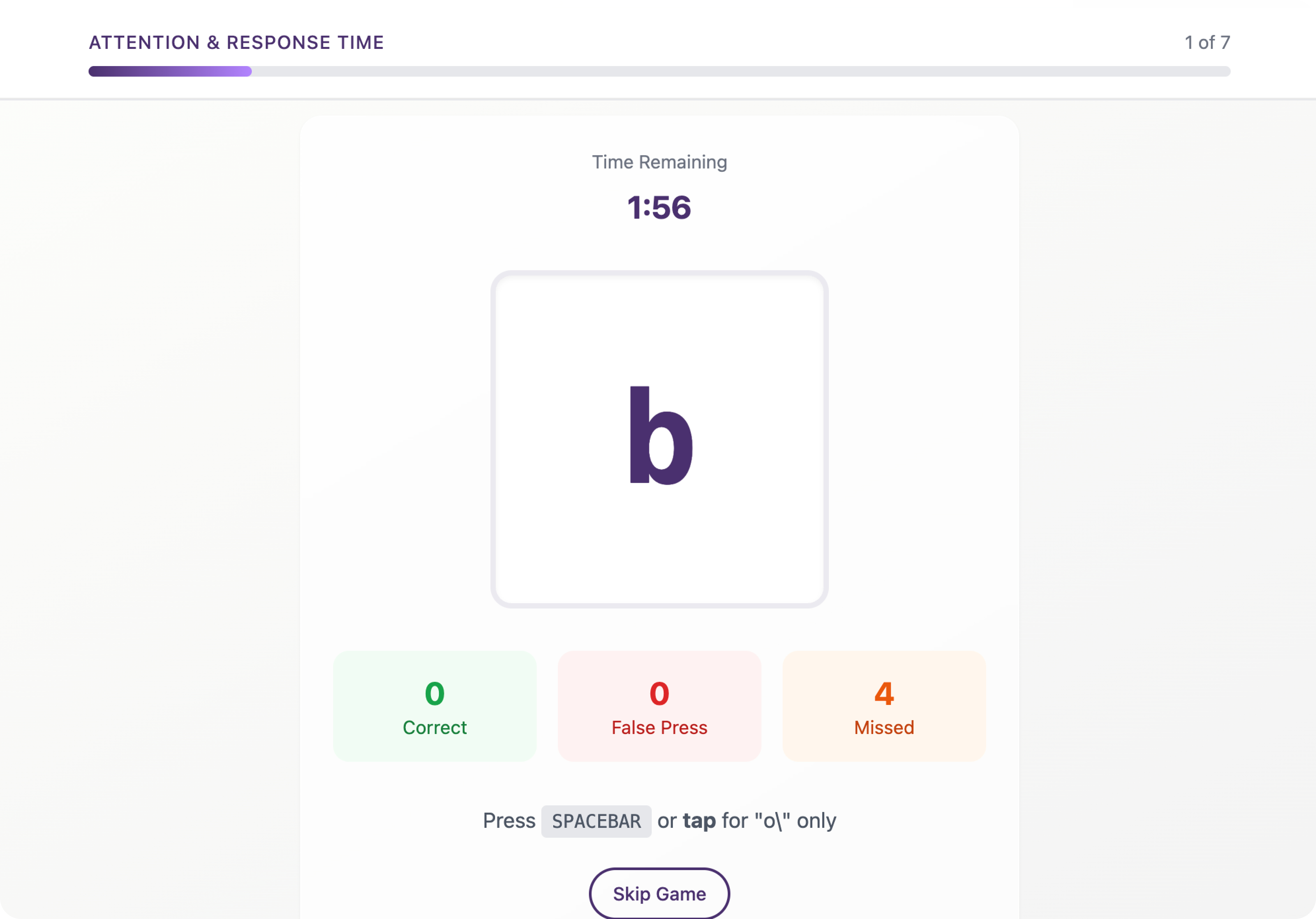
EVALUATE & PREDICT
Cognitive Intelligence Reports
Personalized Cognitive-Cyber Security Reports for organization-wide threats (visible to Administrators) + Risk Breakdowns by department
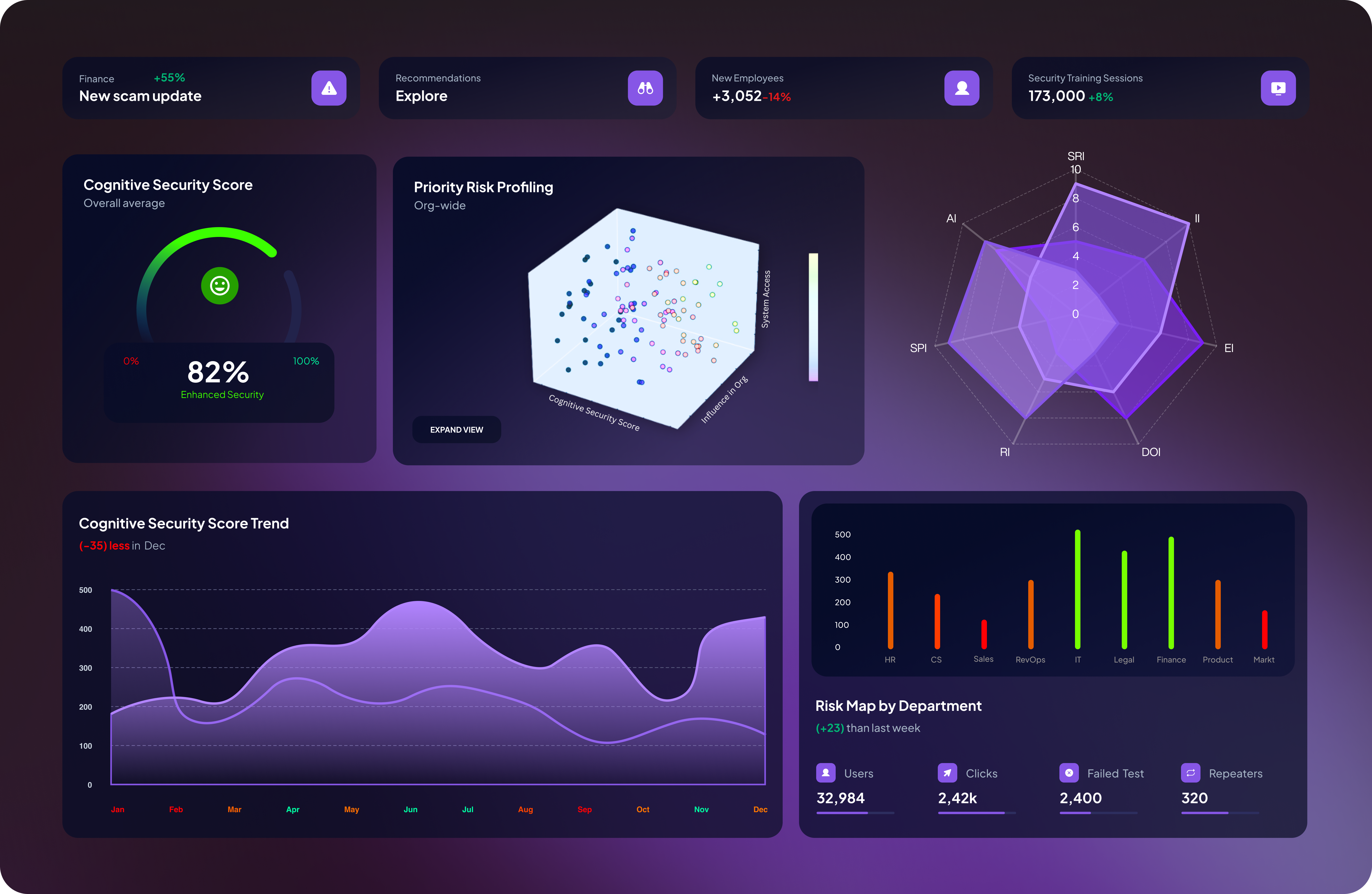
Real-time risk metrics
Live monitoring of cognitive vulnerabilities
Behavioral trend analysis
Pattern recognition across your organization
ROI tracking
Measure security investment returns
Compliance reporting
Automated regulatory documentation
EMPLOYEE EMPOWERMENT
Adaptive Training Platform
Personalized cognitive security training that evolves with your team's needs through micro-learning modules and bias-busting exercises.
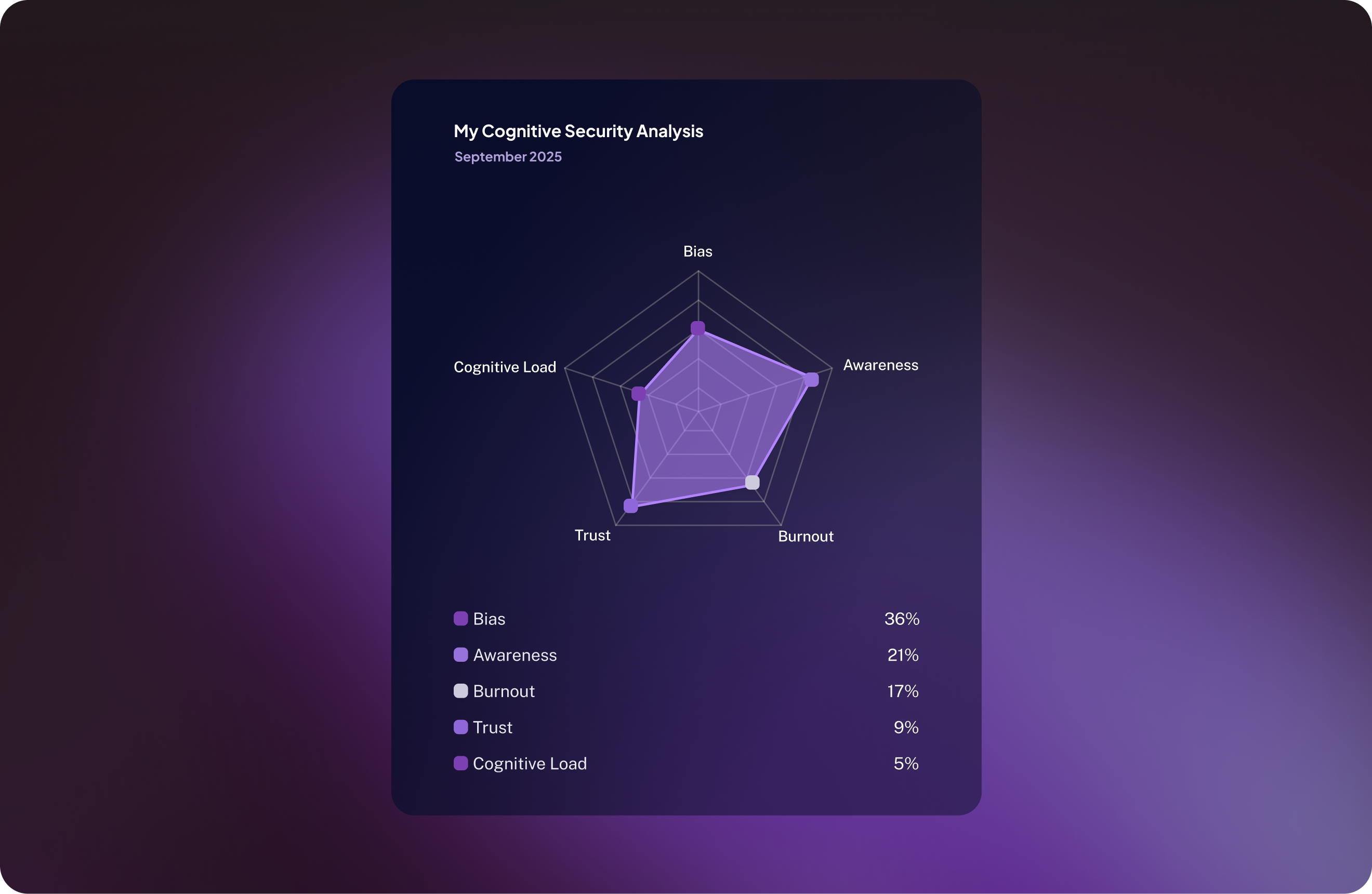
Your Cognitive Profile
The Empathetic Engager
You navigate the world with a deep sense of empathy and a desire for emotional well-being. This makes you compassionate and understanding, but your emotional openness can be a target for those who manipulate feelings for gain.
Adaptive Training Platform
Personalized cognitive security training that evolves with your team's needs.
The sphere of operations, influence, and control will expand from the physical and the information domain to the domain of consciousness; the human brain will become a new combat space.
Ready to Transform Your Security Posture?
Join leading organizations in implementing cognitive security measures that protect against the most sophisticated human-targeted attacks.
Transform Your Security Today
Get started with cognitive security